Contact Us

How To Install and Setup OpenVPN Server On CentOS/RHEL 7?
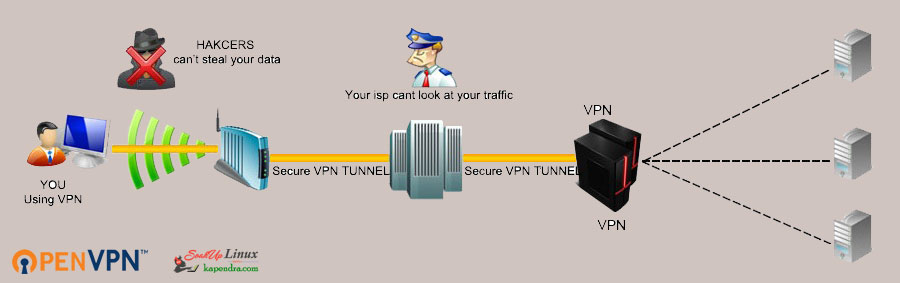
In a server environment is s very important to access servers with security. To implement this network admins or security teams allow specific networks or a list of IPs to get connected. Now all the people within the allowed network are allowed to do several tasks like maintenance work or troubleshooting. But what would happen when you are not in the allowed network and it’s really urgent to get connect with servers. Here we have a need a VPN.
What is OpenVPN?
OpenVPN was first developed under the OpenVPN project/OpenVPN Technologies, Inc. and it was originally developed by James Yonan using C language. Its initial release was 0.90 on the date 13 May 2001. OpenVPN is an open-source software application that uses custom security protocol to set up a VPN by the key exchange over SSL/TLS. It creates secure point-to-point or site-to-site connections. It also Works in routed or bridged configurations and remote access facilities. OpenVPN allows you to traverse through NATs and firewalls.
Working of OpenVPN
OpenVPN allows connections from one network to another using a pre-shared secret key, certificates or username/password. When there is a multi-client-server infrastructure architecture, it allows the server to release an authentication certificate for every client. It uses the OpenSSL encryption library extensively, as well as the SSLv3/TLSv1 protocol, and contains many security and control features.
In this article, we will learn to set up OpenVPN. For this scenario, we will use a system as an OpenVPN server and two client systems, One as a Windows client and the other as a Linux client to test our work.
Note: If you are a SUDO user then prefix every command with sudo, like #sudo ifconfig
If you want to read more articles on OpenVPN then you may follow Given below links
Part 2: How To Install And Setup OpenVPN Server On CentOS/RHEL 6?
Part 3: Setup Linux And Windows Clients To Connect With OpenVPN Server In RHEL/CentOS 6/7
Part 4: How To Add/Create A New OpenVPN Client For OpenVPN Server In CentOS/RHEL 6/7
Part 5: How To Remove Revoke OpenVPN Server’s Clients From OpenVPN Server On RHEL/CentOS 6/7
Part 6: How To Remove OpenVPN Server from CentOS/RHEL 6/7
Scenario
OpenVPN server: 192.168.1.188
Windows client: 192.168.1.18
Linux client: 192.168.1.245
So Let’s start
I did a lot of research and came up with an exact solution. I tried with many tuts present online but none of them was working perfect and without any flaw. So read it completely and do not miss any step.
Step 1: Install Required Repo and packages
Install EPEL repository and some other required packages using the following command
yum install epel-release -y yum install openvpn iptables openssl wget ca-certificates -y
Step 2: Setting UP Easy RSA for Key generation
After packages installation, we need to set up Easy RSA for key generation purposes. This package creates certificates for servers and clients for secure communication. Please follow given below steps.
[root@localhost kapendra]# wget "https://github.com/OpenVPN/easy-rsa/releases/download/3.0.1/EasyRSA-3.0.1.tgz" [root@localhost kapendra]# tar -xvzf EasyRSA-3.0.1.tgz [root@localhost kapendra]# rm -rf EasyRSA-3.0.1.tgz [root@localhost kapendra]# mv EasyRSA-3.0.1/ /etc/openvpn/easy-rsa [root@localhost kapendra]# chown -R root:root /etc/openvpn/easy-rsa/ [root@localhost kapendra]# cd /etc/openvpn/easy-rsa/
Step 3: Create PARAMs, Keys DH with server and client certificates
After EasyRSA set up we will create the PKI followed by setting up CA, the DH params and the server and client certificates using the following commands.
[root@localhost easy-rsa]# ./easyrsa init-pki init-pki complete; you may now create a CA or requests. Your newly created PKI dir is: /etc/openvpn/easy-rsa/pki
Now, Creating a Certificate Authority (certificate + key)
[root@localhost easy-rsa]# ./easyrsa --batch build-ca nopass Generating a 2048 bit RSA private key .....................+++ ....................................+++ writing new private key to '/etc/openvpn/easy-rsa/pki/private/ca.key.L1Hl87i0GX'
Next, generate the Diffie-Hellman file used for information exchange to complement RSA (this will take quite some time)
[root@localhost easy-rsa]# ./easyrsa gen-dh Generating DH parameters, 2048 bit long safe prime, generator 2 This is going to take a long time .................................................+... .....................................+............... ......................+.........++*++* DH parameters of size 2048 created at /etc/openvpn/easy-rsa/pki/dh.pem
Now, creating certificate files for the server.
[root@localhost easy-rsa]# ./easyrsa build-server-full server nopass Generating a 2048 bit RSA private key ..............................+++ ..........+++ writing new private key to '/etc/openvpn/easy-rsa/pki/private/server.key.Rw1LcSsQF6' ----- Using configuration from /etc/openvpn/easy-rsa/openssl-1.0.cnf Check that the request matches the signature Signature ok The Subject's Distinguished Name is as follows commonName :PRINTABLE:'server' Certificate is to be certified until Jul 12 12:37:32 2027 GMT (3650 days) Write out database with 1 new entries Data Base Updated
Finally, create separate certificate files for each client that will use your VPN server. I am considering my CLIENT name is ‘client’ you may change the highlighted bold value with your custom name.
[root@localhost easy-rsa]# ./easyrsa build-client-full client nopass Generating a 2048 bit RSA private key ...............................+++ ..+++ writing new private key to '/etc/openvpn/easy-rsa/pki/private/client.key.lSHPSN5BlE' ----- Using configuration from /etc/openvpn/easy-rsa/openssl-1.0.cnf Check that the request matches the signature Signature ok The Subject's Distinguished Name is as follows commonName :PRINTABLE:'client' Certificate is to be certified until Jul 12 12:39:33 2027 GMT (3650 days) Write out database with 1 new entries Data Base Updated
Also, generate crl.pem along with tls-auth key
[root@localhost easy-rsa]# openvpn --genkey --secret /etc/openvpn/ta.key [root@localhost easy-rsa]# ./easyrsa gen-crl Using configuration from /etc/openvpn/easy-rsa/openssl-1.0.cnf An updated CRL has been created. CRL file: /etc/openvpn/easy-rsa/pki/crl.pem
Step 4: Placing Keys and Permission
To use our newly created servers keys and certificates (except client’s) we need to run the following command.
[root@localhost easy-rsa]# cp pki/ca.crt pki/private/ca.key pki/dh.pem pki/issued/server.crt pki/private/server.key pki/crl.pem /etc/openvpn/
The CRL is read with each client connection when OpenVPN is dropped to nobody to run following.
[root@localhost easy-rsa]# chown nobody:nobody /etc/openvpn/crl.pem
Step 5: Create OpenVPN server.conf File
We need to set up an OpenVPN server.conf file. For do the same copy and paste given below excerpts in your file.
[root@localhost easy-rsa]# vim /etc/openvpn/server.conf
Append the given below line and change highlighted values according to your scenario.
Note: Use the Port Number and Protocol wisely because these ports and protocols will be used in iptables rules.
port 9091 ---------- change the port if you want(default port is 1194) proto udp ---------- choose tcp or udp(recommanded) dev tun sndbuf 0 rcvbuf 0 ca ca.crt cert server.crt key server.key dh dh.pem auth SHA512 tls-auth ta.key 0 topology subnet server 10.8.0.0 255.255.255.0 ifconfig-pool-persist ipp.txt push "redirect-gateway def1 bypass-dhcp" ---- This is to allow All IP traffic like browsing through the VPN push "dhcp-option DNS 8.8.8.8" ---- You may use your Own DNS push "dhcp-option DNS 8.8.4.4" keepalive 10 120 cipher AES-256-CBC comp-lzo user nobody group nobody persist-key persist-tun status openvpn-status.log verb 3 crl-verify crl.pem
Now Save the file using the command :wq!
Step 6: Setup IP Forwarding
Now run the following instructions to set up IP forwarding because we will use port forwarding and NATing for our VPN connection
[root@localhost easy-rsa]# vim /etc/sysctl.conf
Append the following lines
net.ipv4.ip_forward=1
Now Save the file using the command :wq! and to avoid an unneeded reboot run the below command.
[root@localhost easy-rsa]# echo 1>/proc/sys/net/ipv4/ip_forward
Step 8: Setting Up FIREWALLD and rc.local And Starting Service
Now We will set up the Firewall and will some changes to rc.local to finalize our installation. Follow the given below instruction. Also, change the highlighted values with your scenario
vim /etc/rc.d/rc.local
Append the following lines change the bold IP with your VPN server IP
#!/bin/bash ----- relpace #!/bin/sh if there iptables -t nat -A POSTROUTING -s 10.8.0.0/24 ! -d 10.8.0.0/24 -j SNAT --to 192.168.1.188
Save the file using the command :wq! and run the following command to give execution permission.
chmod +x /etc/rc.d/rc.local
Add some Services protocol and ports in the firewall of CentOS 7.
Note: We don’t use –add-service=openvpn because that would only work with the default port and protocol.
[root@localhost easy-rsa]# firewall-cmd --zone=public --add-port=9091/udp [root@localhost easy-rsa]# firewall-cmd --zone=trusted --add-source=10.8.0.0/24 [root@localhost easy-rsa]# firewall-cmd --permanent --zone=public --add-port=9091/udp [root@localhost easy-rsa]# firewall-cmd --permanent --zone=trusted --add-source=10.8.0.0/24
Now Set NAT for the VPN subnet (Change Bold Values With Your VPN server IP and Ports)
[root@localhost easy-rsa]# firewall-cmd --direct --add-rule ipv4 nat POSTROUTING 0 -s 10.8.0.0/24 ! -d 10.8.0.0/24 -j SNAT --to 192.168.1.188 [root@localhost easy-rsa]# firewall-cmd --permanent --direct --add-rule ipv4 nat POSTROUTING 0 -s 10.8.0.0/24 ! -d 10.8.0.0/24 -j SNAT --to 192.168.1.188
After all the changes in our firewall restart the service and
systemctl restart [email protected] systemctl enable [email protected]
This was the server setup so continue reading the next article for Setup Client For OpenVPN
You May Like These Also
Part 1: How To Install And Setup OpenVPN Server On CentOS/RHEL 7?
Part 2: How To Install And Setup OpenVPN Server On CentOS/RHEL 6?
Part 3: Setup Linux And Windows Clients To Connect With OpenVPN Server In RHEL/CentOS 6/7
Part 4: How To Add/Create A New OpenVPN Client For OpenVPN Server In CentOS/RHEL 6/7
Part 5: How To Remove Revoke OpenVPN Server’s Clients From OpenVPN Server On RHEL/CentOS 6/7
Part 6: How To Remove OpenVPN Server from CentOS/RHEL 6/7